A Timeline of Public Key Infrastructure: What Worked, What Failed, and What’s Next
Table of Links
Abstract and I Introduction
II. PKI Problems and Risks
III. Evolution of PKI
IV. National Digital Identity Implementations
V. Conclusion and References
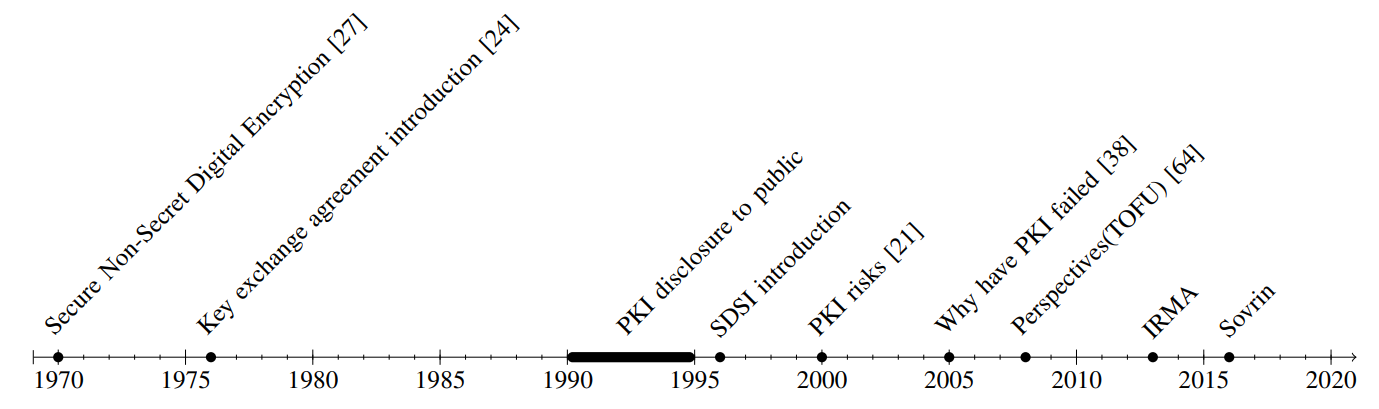
III. EVOLUTION OF PKI
In this chapter, there are presented different views of how the Public Key Infrastructure can evolve and a brief history of alternative systems tried. PKI provides authentication, encryption, and digital signatures, ensuring secure communication, data integrity, and trust in online transactions. From its introduction to the public, alongside the explosion of the World Wide Web, it was only considered from a centralized point of view that had the trust in the Certificate Authorities. The majority of the solutions presented are developing towards a decentralized view of the system, starting as early as 1996 with SDSI, that try to solve some problems from Chapter II. After less than 10 years from its public use, PKI shortcomings were addressed in KeyNote [13], a trust-management system that uses a decentralized approach to handling public key infrastructure, allowing entities to manage their own keys and certificates addressing the scalability and flexibility issues associated with centralized PKIs. The full timeline of events can be observed in Figure 1.
\ A. SDSI
\ SDSI, or A Simple Distributed Security Infrastructure, is an innovative framework designed to address the complexities of security in distributed computing environments [56] tackling the first PKI problem presented while offering a robust and flexible solution, a first step in direction of SPKI(Simple public key infrastructure).
\ One of the most important features of SDSI is its simplicity. It achieves this through clear and intuitive mechanisms that focus on fundamental aspects of security by defining and representing security principles, establishing naming and addressing conventions, and expressing security policies.
\ By providing a straightforward means to define who or what can access resources, SDSI simplifies the task of managing access control. This clarity extends to naming and addressing, enabling a seamless way to locate and identify entities within a distributed network. SDSI recognizes that trust is a foundational element in security, and its framework allows for the establishment of trust among various entities within the system. At the same time, SDSI is the first step towards a decentralized public key infrastructure, allowing entities to make local decisions about access control based on their local policies and knowledge, rather than relying on a central authority for all decisions.
\ While SDSI offers a good step towards a less problematic infrastructure in distributed environments, it’s important to acknowledge that it may not be suitable for all use cases with an accent on digital identity. As state also by the creators of SDSI, ”We feel […] identity certificates must typically in the end be examined by people, to see if the name and other attributes given are consistent with the attributes known to the human reader” [56], the problem of trust is transferred to the issuer(country in our case).
\ Over the years after SDSI design, multiple attempts have been made to use it in more practical ways to be able to overcome the problem of economic reasons. For example, in 1997, one year after SDSI release, a C library was created [28] to pave the way for its usage in different scenarios alongside a Java implementation in 1998 [47] followed by an implementation of a secure web client using SPKI/SDSI certificates [46] in 2000, to meet the growing importance of the World Wide Web and with a case study on the effect on a company.
\ B. Perspectives(TOFU)
\ Trust-on-first-use(TOFU) is a strategy where, during the first encounter with a server or system, the user accepts and stores its public key without explicit verification. Subsequent connections are allowed only if the presented key matches the stored key, being a pragmatic approach to bootstrapping trust in a key-based authentication system. From its introduction to Secure Shell protocol, TOFU was seen as an improvement to the PKI ecosystem from 2008 with Perspectives [64], with no certificate authority needed to verify the identity of server owners and grant them certificates. The validity of a service’s key is determined by its existence on the network over time. Perspectives system helps mitigate man-in-the-middle attacks by providing users with a more reliable basis for trust in the presented server public key.
\ However, the infrastructure inherits problems from the TOFU protocol, assuming that the initial connection is secure and that the user can trust the initial public key received during the first connection. If an attacker can compromise this initial connection, they may be able to present a malicious key that Perspectives would then consider as legitimate. The Perspectives system relies on a network of notary servers distributed across the Internet, presenting a new decentralized solution of PKI. Implementing and maintaining a network of notary servers can be complex and the effectiveness of Perspectives relies on widespread adoption and a sufficient number of notaries to provide diverse perspectives. Achieving and sustaining this level of adoption can be challenging and can increase the already complex infrastructure.
\ C. IRMA
\ IRMA stands for ”I Reveal My Attributes” and is a project aimed at implementing attribute-based identity management that seeks to address issues related to attributes, their possibilities, and challenges [6].
\ The paper acknowledges the existence of cryptographic techniques for secure and privacy-friendly attribute-based authentication, noting that recent advancements in smart card technology have made it possible to deploy attributes in practical scenarios. The concept of attributes [7] is used broadly
\ 
\ to describe the properties of individuals. These attributes may range from anonymous attributes (non-identifying), such as gender or age, to identifying attributes, like bank account or social security numbers. The paper highlights that while the underlying technology ensures full unlinkability, attribute values may allow for linkability expanding the range of application scenarios. It relies on the Idemix technology and uses personal smart cards as carriers of credentials and attributes.
\ The extensive use of attributes within IRMA leads to dependencies between attributes, where the issuance of one attribute may depend on the verification of another. These dependencies give rise to a tree structure for attributes and raise questions about what should be considered ”root” attributes that do not depend on others. These considerations have implications for societal identity structures, including pseudonym accounts.
\ The paper suggests the involvement of an independent, nonprofit foundation to manage the IRMA scheme, set policy, and oversee certificate management for access to the card. This foundation would play a crucial role in addressing sensitive issues related to attribute management and policy solving perhaps the economic and legal problem of monopoly of a company on a scheme.
\ More work has been added to the IRMA project, with an implementation for smartphones [8] in 2017 to facilitate its usage by ordinary people (with an app and QR codes) but also for service providers using standardized JSON Web Tokens. In 2019, solutions were proposed to contribute to ensuring the confidentiality and integrity of IRMA credentials in various scenarios. ”Backup and Recovery of IRMA Credentials” [23] emphasizes that a recovery solution for IRMA should be designed as a backup and restore mechanism. To enhance portability and user-friendliness, the backup should be encrypted in a way that allows storage in any location without imposing a specific storage location on the user.
\ In this, key management is a crucial aspect of the design. The primary solution involves using a mnemonic phrase that can be written down on paper, an approach that does not require technical expertise and is understandable to users. Additionally, parts of the key are managed by trustees or a trusted institution as a second authentication factor to enhance security.
\ D. Soverin
\ Security requirements for digital identity systems mirror those of traditional paper credentials, encompassing compatibility, unforgeability, scalability, low latency, and revocation capabilities. Digital identity systems offer advantages like minimal dependencies, privacy/anonymity, unlinkability, and selective disclosure, providing a level of control impossible in paper-based systems.
\ Privacy-oriented digital identity schemes, such as U-Prove and Idemix, have been proposed but face challenges in widespread adoption due to issues like compatibility and scalability. For that, Sovrin is a system that integrates anonymous credentials with revocation, emphasizing privacy, unforgeability, performance, and unlinkability. The implementation incorporates a distributed ledger inspired by Ethereum and Byzantine Fault Tolerant (BFT) protocols for scalability [66].
\ Sovrin employs anonymous credentials based on zeroknowledge proofs, providing unlinkability and features like delegation and revocation. Privacy concerns are associated with revocation, but in [40] paper, attribute-based sharding are proposed to enhance privacy during the revocation process(and closing the gap to IRMA). The revocation methods involve cryptographic accumulators for efficiency.
\ Overall, Sovrin aims to address privacy and security concerns in digital identity systems through its innovative design and implementation and states from its requirements ”selfsovereign identity, where every person, organization, or thing can have its own truly independent digital identity that no other person, company, or government can take away” [55]. Furthermore, the paper explains what most distinguishes Sovrin as a distributed identity system: it is the first public permissioned ledger. The stack of the technology has 3 important levels: Sovrin Ledger, Sovrin Agents and Sovrin Clients.
\ In a comparison between IRMA and Sovrin [48], adopting Sovrin is considered challenging for both service providers and credential users and, like the PKI, its commercial value can be overseen. At the same time, Sovrin is a complex project and still in progress with its documentation, being an open source, being somewhat scattered around. However, Sovrin has an advantage over IRMA in deployment in such that service providers do not need to host any server because of the Sovrin Ledger. Regarding the digital identity problem, Sovrin has been cited as a possible solution for the technology needed in such schemes [67].
\
:::info Authors:
(1) Adrian-Tudor Dumitrescu, Delft University of Technology, Delft, The Netherlands (A.T.Dumitrescu@student.tudelft.nl);
(2) Johan Pouwelse (thesis supervisor), Delft University of Technology, Delft, The Netherlands (J.A.Pouwelse@tudelft.nl).
:::
:::info This paper is available on arxiv under CC BY 4.0 DEED license.
:::
\
You May Also Like

Microsoft Corp. $MSFT blue box area offers a buying opportunity

IP Hits $11.75, HYPE Climbs to $55, BlockDAG Surpasses Both with $407M Presale Surge!
