Crypto Community Underattack: New X Account Takeover Threat

Crypto security experts have identified a recently emerged, sophisticated phishing campaign targeting prominent figures on X (formerly Twitter). Unlike traditional scams, this campaign employs advanced tactics that bypass two-factor authentication, making it particularly dangerous. The attack leverages X’s own infrastructure to gain unauthorized access to high-profile accounts, raising concerns about emerging vulnerabilities within social media platforms used heavily by the crypto community.
- A new phishing campaign targets crypto personalities’ X accounts by exploiting X’s infrastructure to bypass two-factor authentication.
- The attack uses convincing messaging and metadata tricks, creating highly credible phishing links mimicking Google Calendar.
- Experts warn that the campaign could be part of a broader effort to compromise social media accounts in the crypto sector.
- The scam involves a fake authorization request that demands extensive account permissions, raising suspicion among vigilant users.
- Recommendations include revoking suspicious connected apps and carefully examining unusual permission requests to prevent account compromise.
A new wave of phishing campaigns is targeting the social media accounts of industry figures within the cryptocurrency community, posing an increasing threat in the digital asset ecosystem. These scams have demonstrated the ability to sidestep two-factor authentication, utilizing X’s own infrastructure for account takeover. This method underscores the evolving sophistication of attack vectors aimed at crypto influencers and traders, whose accounts often hold significant value in the market.
As reported by crypto developer Zak Cole, the attack does not rely on conventional means like fake login pages or password theft. Instead, it exploits support features within the X app itself, stealing account control without requiring the victim’s password or 2FA. This has prompted a warning from security researchers and prompted calls for heightened vigilance. MetaMask security researcher Ohm Shah confirmed seeing the attack active “in the wild,” indicating a potentially wide-ranging campaign, with a less sophisticated version targeting an OnlyFans model.
Crafting a convincing phishing message
The campaign’s standout feature is its ability to appear authentic. Attackers initiate contact through direct messages containing links that seem to direct users to legitimate services. The links appear to lead to the Google Calendar domain, thanks to how X generates post previews using metadata. In reality, the link directs to a domain registered as “x(.)ca-lendar(.)com,” registered only days prior, but the preview shows the familiar Google Calendar URL, tricking users into trusting the link.
Once clicked, the link redirects to an X authorization page requesting permission for an app called “Calendar” to access the account. Closer inspection reveals the app’s name includes two Cyrillic characters that resemble Latin “a” and “e,” a subtle trick designed to evade detection. The authorization request then prompts users to grant extensive permissions, including following accounts, posting, editing profile info, and more—all of which are suspicious for a calendar app.
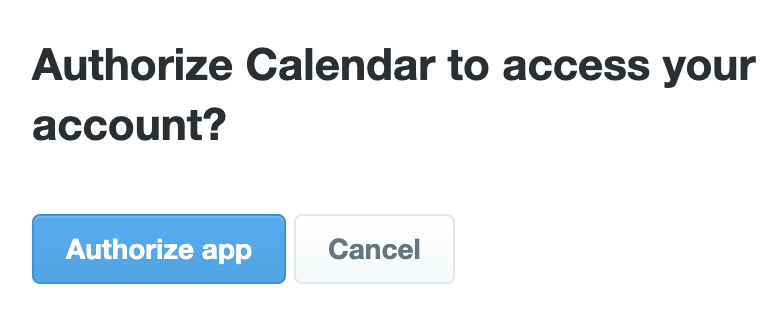 Fake authorization request for the phishing app. Source: Zak Cole
Fake authorization request for the phishing app. Source: Zak Cole
Detecting the signs of a phishing attack
One of the most subtle signs of the scam is a fleeting appearance of the URL—likely visible for only a moment before redirection—making it easy to overlook. However, a key indicator is the scope of requested permissions. The app seeks control over nearly every aspect of the account—from posting to managing followers—which is highly unusual for a calendar app.
Adding to the suspicion, users are redirected to Calendly.com after granting permission, revealing an inconsistency that should prompt skepticism. “They spoofed Google Calendar but redirected to Calendly? Operational security failure,” Cole noted. To prevent account compromise, he recommends reviewing connected apps on X’s settings page and revoking any called “Calendar,” especially those that seem suspicious.
This attack’s complexity illustrates the importance of maintaining a cautious stance towards social media permissions, especially within the cryptocurrency sphere where influential accounts can significantly sway market sentiment. As crypto markets remain volatile, securing these digital assets from social engineering tactics is more critical than ever.
This article was originally published as Crypto Community Underattack: New X Account Takeover Threat on Crypto Breaking News – your trusted source for crypto news, Bitcoin news, and blockchain updates.
You May Also Like

IP Hits $11.75, HYPE Climbs to $55, BlockDAG Surpasses Both with $407M Presale Surge!
Academic Publishing and Fairness: A Game-Theoretic Model of Peer-Review Bias
