CrossCurve Contains Exploit: Crypto Thefts Create January Ruckus
CrossCurve, the decentralized finance protocol formerly known as EYWA, confirmed that it stopped a bridge exploit tied to its cross-chain token system on Sunday. The attack targeted the Ethereum side of the bridge and led to unauthorized token releases after a smart contract flaw was abused.
The team stated that the attacker pulled EYWA tokens from the Ethereum bridge contract. Those tokens cannot move or be sold. Only one centralized venue had an Ethereum ETH $2 298 24h volatility: 4.2% Market cap: $277.73 B Vol. 24h: $56.21 B deposit channel for EYWA, and that deposit route has been frozen. Tokens on Arbitrum were not affected, and no fresh supply entered the market.
CrossCurve also contacted all centralized exchanges where EYWA trades, including KuCoin, Gate, MEXC, BingX, and BitMart. The goal was to block any exit path for the stolen tokens. The protocol said the stolen EYWA supply cannot circulate and will not impact the token supply or price.
Addresses Flagged, Legal Clock Starts
The same day, CrossCurve confirmed it tracked ten Ethereum addresses tied to the exploit. According to the team, funds moved into these wallets due to a smart contract failure in the bridge logic, not user error.
Management stated the wallets have 72 hours to return the funds or make contact. If that window closes, the case will turn into a legal battle. That includes criminal referrals, civil action, public wallet disclosure, and coordination with exchanges, token issuers, law enforcement, and blockchain tracking firms.
How the Exploit Worked
Security firms said the attack used a fake cross-chain message that bypassed validation checks in the bridge contract. That message triggered token releases across multiple chains.
Defimon Alerts estimated losses near $3 million across several networks. BlockSec placed total losses closer to $2.76 million. Its breakdown showed about $1.3 million on Ethereum, $1.28 million on Arbitrum, and smaller amounts across Optimism, Base, Mantle, Kava, Frax, Celo, and Blast.
https://twitter.com//status/2018167679300104449?s=20
January Creates Ruckus
The CrossCurve incident landed during the most aggressive theft month in nearly a year. CertiK data showed $370.3 million stolen through exploits and scams in January. That was the highest monthly figure in 11 months and nearly four times higher than January 2025.
One social engineering case alone accounted for roughly $284 million. Phishing activity made up $311.3 million of total losses for the month. January marked a 277% jump from January 2025, when losses totaled $98 million. It also exceeded December losses of $117.8 million by more than 200%.
The largest technical hack of the month was the Step Finance breach, where attackers took $28.9 million after treasury wallets were compromised and more than 261,000 SOL was drained.
nextThe post CrossCurve Contains Exploit: Crypto Thefts Create January Ruckus appeared first on Coinspeaker.
You May Also Like
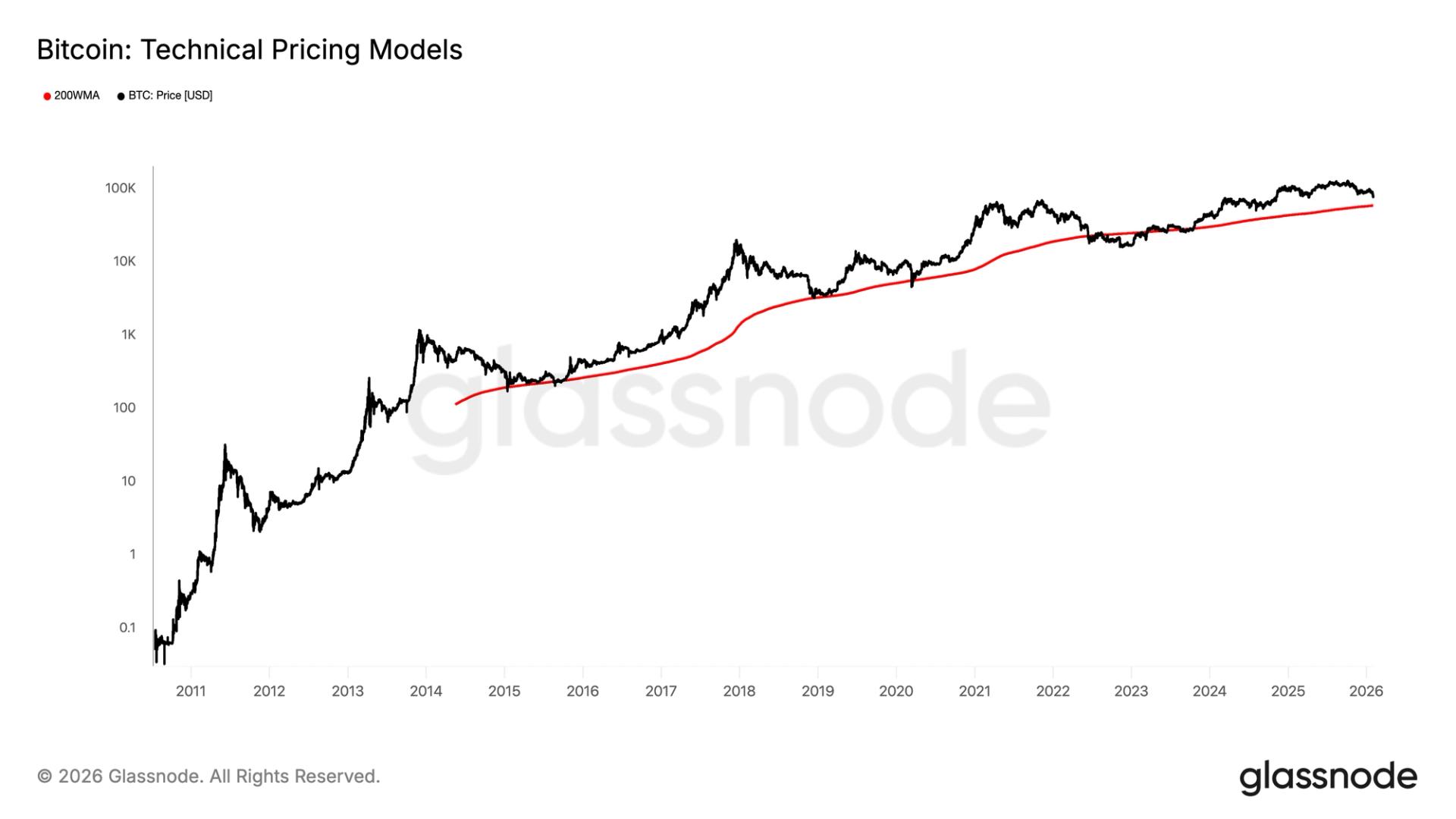
Why a $58,000 bitcoin is the key number for crypto investors right now
Copy linkX (Twitter)LinkedInFacebookEmail
Virtune AB (Publ) (“Virtune”) has completed the monthly rebalancing for January 2026 of its Virtune Crypto Altcoin Index ETP

