PANews reported on November 23 that Port3 Network released an incident report on its X platform regarding a hacking attack. Port3 Network stated that it used NEXA Network's cross-chain token solution, CATERC20. However, CATERC20 has a boundary condition verification vulnerability. After token ownership was relinquished, the function returned a value of 0, which happens to match the ownership verification condition. Therefore, the ownership check failed, making unauthorized access possible. This issue was not mentioned in the CATERC20 audit report. Because Port3 tokens had previously relinquished ownership to achieve greater decentralization, they were in this vulnerable state.PANews reported on November 23 that Port3 Network released an incident report on its X platform regarding a hacking attack. Port3 Network stated that it used NEXA Network's cross-chain token solution, CATERC20. However, CATERC20 has a boundary condition verification vulnerability. After token ownership was relinquished, the function returned a value of 0, which happens to match the ownership verification condition. Therefore, the ownership check failed, making unauthorized access possible. This issue was not mentioned in the CATERC20 audit report. Because Port3 tokens had previously relinquished ownership to achieve greater decentralization, they were in this vulnerable state.
Port3 Network: Attacked due to a boundary condition verification vulnerability in its cross-chain token solution CATERC20.
PANews reported on November 23 that Port3 Network released an incident report on its X platform regarding a hacking attack. Port3 Network stated that it used NEXA Network's cross-chain token solution, CATERC20. However, CATERC20 has a boundary condition verification vulnerability. After token ownership was relinquished, the function returned a value of 0, which happens to match the ownership verification condition. Therefore, the ownership check failed, making unauthorized access possible. This issue was not mentioned in the CATERC20 audit report. Because Port3 tokens had previously relinquished ownership to achieve greater decentralization, they were in this vulnerable state.
Disclaimer: The articles reposted on this site are sourced from public platforms and are provided for informational purposes only. They do not necessarily reflect the views of MEXC. All rights remain with the original authors. If you believe any content infringes on third-party rights, please contact service@support.mexc.com for removal. MEXC makes no guarantees regarding the accuracy, completeness, or timeliness of the content and is not responsible for any actions taken based on the information provided. The content does not constitute financial, legal, or other professional advice, nor should it be considered a recommendation or endorsement by MEXC.
You May Also Like

Fed Lowers Rates By 25bps: How Bitcoin And Crypto Prices Responded And What’s Next
The Federal Reserve (Fed) announced its first interest rate cut of the year, leading to an immediate reaction in the cryptocurrency market. Bitcoin (BTC) experienced a notable decline, dropping below the $115,000 threshold shortly after the announcement. Expert Predicts Crypto Rally Fed Chair Jerome Powell addressed the current economic landscape, noting that while inflation has […]
Share
Bitcoinist2025/09/18 03:11

Filecoin Breakout Alert: Analysts Eye Explosive Jump Toward $15 and $30
Filecoin (FIL) is currently trading at $1.46, marking a 6.62% decline over the past 24 hours, while its trading volume rose slightly to $139.65 million, an increase of 1.16%. The token has also dropped 10.32% over the past week, reflecting persistent downward pressure across the decentralized storage sector. Despite the short-term weakness, market observers note […]
Share
Tronweekly2025/12/06 07:00
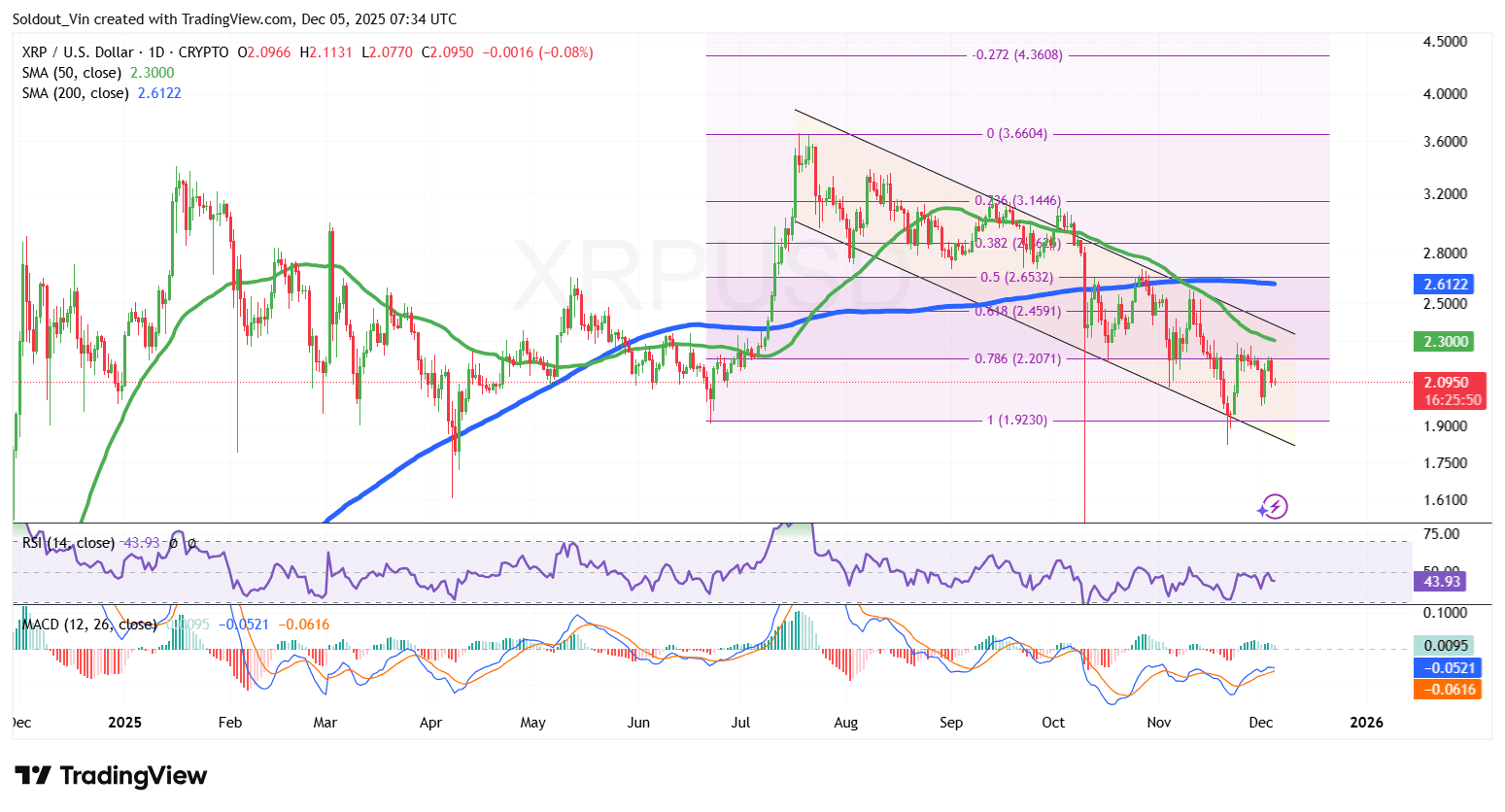
XRP Price Plunges 3.5% As Santiment Says Soaring FUD May Spark A Rally
The International Monetary Fund (IMF) warned that rising stablecoin adoption could weaken central banks’ control over monetary policy and threaten nations’ financial sovereignty. While stablecoin [...]
Share
Insidebitcoins2025/12/05 18:45