Truebit Protocol Hacker Launders All $26M in ETH After Major Exploit
This article was first published on The Bit Journal.
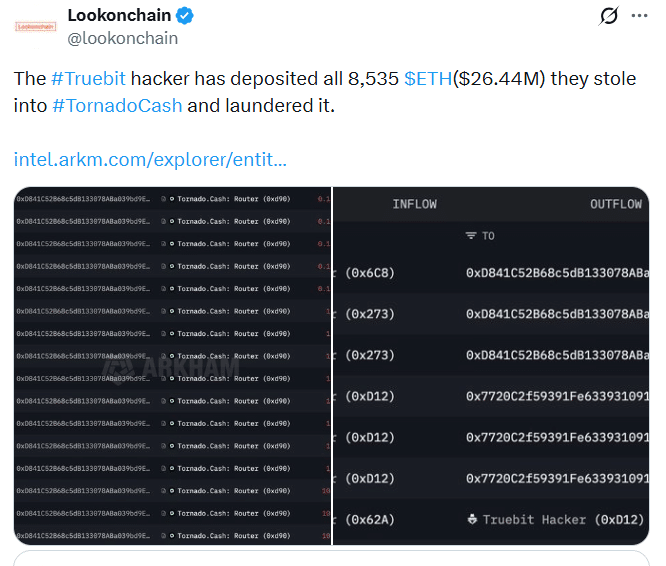
The Truebit hacker has laundered all 8,535 ETH stolen in the Truebit Protocol hack, worth about $26 million. On-chain trackers said the funds were routed through Tornado Cash after the attacker exploited a smart contract flaw on January 8.
The Truebit Protocol hack began when the attacker abused an integer overflow in a legacy smart contract. Investigators said the flaw allowed the hacker to mint millions of TRU tokens at almost zero cost.
The attacker then sold those tokens back into the protocol repeatedly. This cycle drained ETH liquidity within a short window.
Two Addresses Linked to Stolen ETH Transfers
The stolen ETH moved through two main addresses before laundering. Trackers flagged 0x2735…cE850a and 0xD12f…031a6 as the core wallets involved in the transfer chain. Within hours, the exploit also crushed TRU’s value across exchanges.
 Source: X
Source: X
Analysts said the Truebit Protocol hack followed a classic smart contract failure pattern. The attacker did not need compromised private keys.
Also Read: What Trust Wallet’s $7M Hack Reveals About SME Crypto Security Risks
The weakness was inside the contract logic itself. This enabled the hacker to generate TRU supply artificially. It also allowed repeated swaps that emptied the protocol’s ETH reserves.
After the extraction stage, the laundering phase started quickly. Tornado Cash was used to reduce traceability. This move has lowered the chances of recovery.
What triggered the exploit in the Truebit Protocol hack
Security researchers said the Truebit Protocol hack centered on unsafe arithmetic. Integer overflow issues can distort internal calculations. This can break pricing logic and minting limits.
The attacker used this weakness inside a legacy contract. That created an entry point for low-cost token creation. Once the minting was possible, the exploit scaled fast.
How minting cycles drained ETH reserves
On-chain activity suggests the hacker minted TRU tokens at near-zero cost. The attacker then sold them into the protocol’s bonding curve. That pushed ETH out of the liquidity pool.
The loop repeated many times. Each cycle weakened reserves. Each sale increased pressure on the token market. This is why the Truebit Protocol hack caused both liquidity damage and a token collapse.
TRU token crash wiped out the market value
The Truebit Protocol hack caused TRU to crash almost immediately. Market data showed the token dropped nearly 100% within hours. It also became close to worthless on most exchanges soon after.
Traders said the collapse was expected once liquidity drained. Thin pools cannot absorb constant pressure. Once reserves fall too low, price discovery breaks.
Tornado Cash laundering removed easy traceability
Lookonchain data indicated the attacker laundered the entire 8,535 ETH. Tornado Cash was used as the final step. That choice is common in DeFi theft cases.
Mixers split the transaction trail. They also make fund tracking harder. Some tracing is still possible. But attribution becomes far more complex after mixing.
Wallet trail and key addresses flagged
On-chain trackers linked the stolen ETH to two main addresses. These were 0x2735…cE850a and 0xD12f…031a6. Analysts said both wallets served as staging points.
Funds were moved, split, and later consolidated. That behavior often signals a skilled actor. This pattern is also seen in other major DeFi exploits.
PeckShield links actor to Sparkle exploit
PeckShield said the Truebit Protocol hack may be tied to the same hacker behind Sparkle. That earlier incident happened about two weeks before. It followed a similar method.
In the Sparkle case, the attacker exploited minting logic. Tokens were created at an artificial discount. They were swapped into ETH quickly. Funds later moved through Tornado Cash.
Truebit response and law enforcement contact
The Truebit team said it is aware of the issue. It advised users not to interact with the affected contract. The team also said it contacted law enforcement. It has started a broad internal review.
A full post-mortem has not been released yet. Analysts said a technical report will be important. It could clarify the exact weakness. It could also show what controls failed.
Wider context as crypto hacks surged in 2025
The Truebit Protocol hack comes after a record year for crypto theft. TRM Labs estimated more than $2.72 billion was stolen in 2025. The year also included the Bybit theft worth $1.5 billion. That was the largest exploit recorded.
Chainalysis recently warned of growing professionalization. It said illicit organizations now run structured on-chain systems. Chainalysis also reported illicit addresses received at least $154 billion in 2025. A large share was linked to sanctioned entities.
Conclusion
The Truebit Protocol hack moved quickly from exploitation to laundering. The attacker drained ETH reserves, crushed TRU’s price, and used Tornado Cash to hide the trail. The case highlights the risks of legacy smart contracts.
It also shows how fast liquidity attacks can unfold in DeFi. Until a full post-mortem is published, users are likely to remain cautious about interacting with the protocol.
Also Read: Crypto Hack Loss Drop 60% in December to $76M, PeckShield Reports
Appendix: Glossary of Key Terms
Truebit Protocol: A blockchain protocol involved in the reported DeFi incident.
Truebit Protocol hack: The exploit that drained ETH by abusing a smart contract weakness.
Smart Contract: Self-executing blockchain code that automates transactions and rules.
Integer Overflow: A coding flaw where values exceed limits and distort calculations.
Pricing Logic: Contract rules that determine token price during buys and sells.
Bonding Curve: A mechanism that adjusts token price based on supply changes.
Token Minting: The creation of new tokens through a protocol’s contract function.
Liquidity Drain: Rapid removal of ETH reserves caused by repeated swaps or sells.
Frequently Asked Questions About Truebit Protocol Hack?
1- What happened in the Truebit Protocol hack?
A hacker exploited a legacy smart contract weakness, minted TRU tokens cheaply, and drained ETH from the protocol.
2- How much ETH was stolen?
The attacker stole 8,535 ETH, valued at about $26 million at the time.
3- Why did TRU crash so hard?
The exploit drained liquidity and created massive sell pressure. The market could not absorb it.
4- Why was Tornado Cash used?
It was used to hide the transaction trail. This makes fund recovery harder.
References
CryptoBriefing
CryptoPotato
Read More: Truebit Protocol Hacker Launders All $26M in ETH After Major Exploit">Truebit Protocol Hacker Launders All $26M in ETH After Major Exploit
You May Also Like

Wall Street’s Pivotal Shift To Digital Asset Leadership
Introducing ZED Picks: A First-of-its-Kind Pick-and-Play Digital Horse Racing Game
