Nemo Protocol Loses $2.4M to Hackers on Sui Blockchain Before Planned Maintenance
Nemo Protocol, a decentralized finance (DeFi) yield platform operating on the Sui blockchain, fell victim to a cyberattack that resulted in $2.4 million in losses just ahead of its scheduled maintenance window on Monday and Tuesday.
The security breach was initially detected by PeckShieldAlert on September 8, which reported via X that approximately $2.4 million in USDC had been drained from Nemo’s systems.
According to the blockchain security firm’s investigation, the hacker swiftly moved the stolen assets via Circle by bridging USDC on Arbitrum to Ethereum.
$6.3M TVL Crashes 75% as Users Flee Nemo Protocol
Nemo acknowledged the incident in a subsequent tweet, stating that the protocol had experienced a security breach the previous evening that affected its Market pool.
The development team confirmed that an investigation was in progress to identify the root cause of the vulnerability.
As a precautionary measure, all smart contract operations were temporarily halted.
The attack’s impact was immediately felt. According to DeFiLlama data, Nemo’s total value locked (TVL) collapsed to approximately $1.57 million from over $6.3 million before the breach.
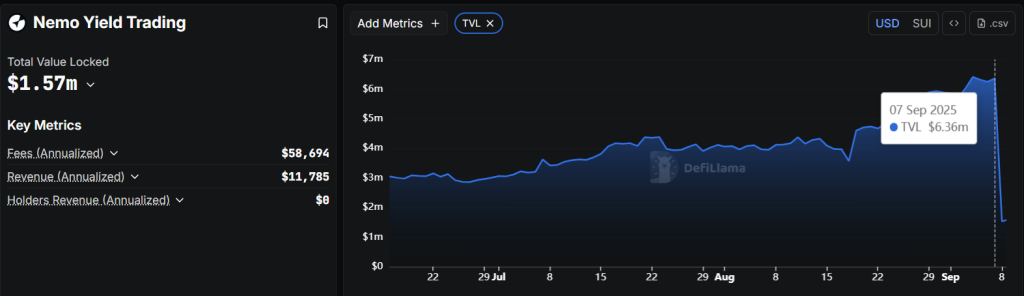 Source: DefilLama
Source: DefilLama
User withdrawals exceeded $3.8 million worth of USDC and SUI tokens as investors rushed to exit, fearing the exploit’s scope might be more extensive than initially disclosed.
The breach specifically targeted Nemo’s yield-trading mechanism, which enables users to divide staked assets into Principal Tokens (PTs) and Yield Tokens (YTs) for yield speculation purposes.
According to blockchain security auditor CertiK, security risks may arise from multiple sources, including coding errors, blockchain network vulnerabilities, and programming language limitations.
Sui Blockchain Security Crisis Contributed to $2.37 Billion DeFi Losses in 2025
Notably, the Nemo security breach marks the third major hack targeting DeFi protocols this month.
Earlier in September, Venus protocol lost $13.5 million to attackers, followed by an $8.4 million theft from the Bunni protocol.
Similarly, in the Sui ecosystem, the Nemo incident follows another significant breach on the Layer-1 network from earlier this year.
On May 22, Cetus Protocol, a prominent decentralized exchange and liquidity provider, suffered a $223 million exploit.
The attacker leveraged an arithmetic overflow flaw in a third-party code library to complete the drain within 15 minutes.
Moreover, these DeFi-focused attacks are on the rise in 2025.
SlowMist’s mid-year analysis revealed that the blockchain sector experienced over $2.37 billion in losses across 121 security incidents during the first half of the year.
DeFi protocols alone accounted for 76% of these cases, although centralized exchanges recorded higher individual losses.
A complementary report from Hacken’s 2025 mid-year security assessment estimated total crypto industry losses at over $3.1 billion within the first six months.
Access control vulnerabilities, including misconfigured wallets and compromised legacy keys, represented 59% of these losses, while DeFi-specific smart contract exploits accounted for $263 million, or roughly 8%.
A recent interview between Cryptonews and Mitchell Amador, founder and CEO of Immunefi, highlighted why conventional security methodologies prove inadequate in Web3’s open-source ecosystem.
Amador explained that “Traditional audits, being static and pre-launch focused, fail to identify post-deployment vulnerabilities present in dynamic DeFi environments.”
He advocated for bug bounty programs as a solution to incentivize ethical hackers, fundamentally restructuring cybersecurity economics to make defensive measures more lucrative than offensive ones.
You May Also Like

Aave DAO to Shut Down 50% of L2s While Doubling Down on GHO

The "1011 Insider Whale" has added approximately 15,300 ETH to its long positions in the past 24 hours, bringing its total account holdings to $723 million.

